For us, we just want to get on with the programming. But what if something is welling up, that might stop you “getting on”?
We saw this on our “soon to be” dedicated virtual AlmaLinux Apache/PHP/MySql web server, for RJM Programming, where we use SSH (Secure Shell) to access and get to a command line environment on that AlmaLinux web server via (no secret anymore) …
ssh -p 22 root@65.254.95.247
But what is a secret is the ensuing password needed to log in. Worrying us, though, lately, was dialog such as …
user@MacBook-Air htdocs % ssh -p 22 root@65.254.95.247
root@65.254.95.247’s password:
Last failed login: Fri Aug 2 20:49:45 EDT 2024 from 180.184.139.166 on ssh:notty
There were 157 failed login attempts since the last successful login.
Last login: Fri Aug 2 19:20:56 2024 from 60.227.219.39
[root@65-254-95-247 ~]# exit
logout
… “greeting” us as we logged in. We dislike the advice online to configure SSH access away from port 22 (though we’re sure it could help some), so? If you’re into security you will know the term “SSH Brute Force Attack” …
An SSH brute force attack is a hacking technique that involves repeatedly trying different username and password combinations until the attacker gains access to the remote server.
Well, yes, our password is good, but if you were me, would you want to put up with this when, given the way you can trust yourself with the remembering of your own high security passwords, you have these great informative, and reassuring, websites like Fail2Ban install tutorial for Linux (AlmaLinux) that give you great step by step ways to …
- on AlmaLinux style web server …
- as required, install (oh, that’s what that is … from CentOS roamings) “fail2ban” and “firewalld” (we touched on the “feel for” with previous CentOS based WHM cPanel cPHulk Firewall Primer Tutorial) … and then, the all important (and we recommend if all this is new, to take the advice of others) …
- configure fail2ban and fail2ban-client and arrangements regarding ssh login access
… is there to help you out? And, yes, Aristotle, that last question was rhetorical.
Previous relevant WHM cPanel cPHulk Firewall Primer Tutorial is shown below.
For our CentOS Linux Apache/MySql/PHP web server for RJM Programming, we needed to reboot the Apache and MySql services, via the use of an unusual (at least for us, because we couldn’t get graphical WHM cPanel access working) combination of …
- Power Management … Stop and Start the VMWare Virtual Host … followed by …
- ssh command line access means by which to restart Apache and MySql services (and we like this link as a services list checklist, thanks) via …
service http restart
service mysql restart
… and even a …
service cpanel restart
… would not allow our graphical based WHM cPanel access happen, us getting, instead, when trying to access the usual Safari web browser address bar way, the error message …
The connection timed out. Please try again.
Weird! Anyway, researching this (but please note all along, we suspect we may have been able to solve the issue by closing the Safari web browser and reopening and retrying it) we got onto the topic of …
Web Server Firewalls
… associated with (what might be a “service” for you) cPanel’s cPHulk software.
We looked into cPHulk, and decided to Stop and Start cPHulk finding great “Stop” advice here, getting us to go, while still in ssh session …
/usr/local/cpanel/etc/init/stopcphulkd
rm -f /var/cpanel/hulkd/enabled
… then changed devices to see whether we could get a graphical cPanel session going, and, lo and behold, and relieved, yes, we could!
But then there was the “Start” bit to the cPHulk work here. Up the top left of graphical cPanel we typed in “cPHulk” and got to the webpage …
cPHulk Brute Force Protection
… where we were surprised (and saddened) to see an error message …
The cphulkd login table seems corrupted. Please contact your system administrator.
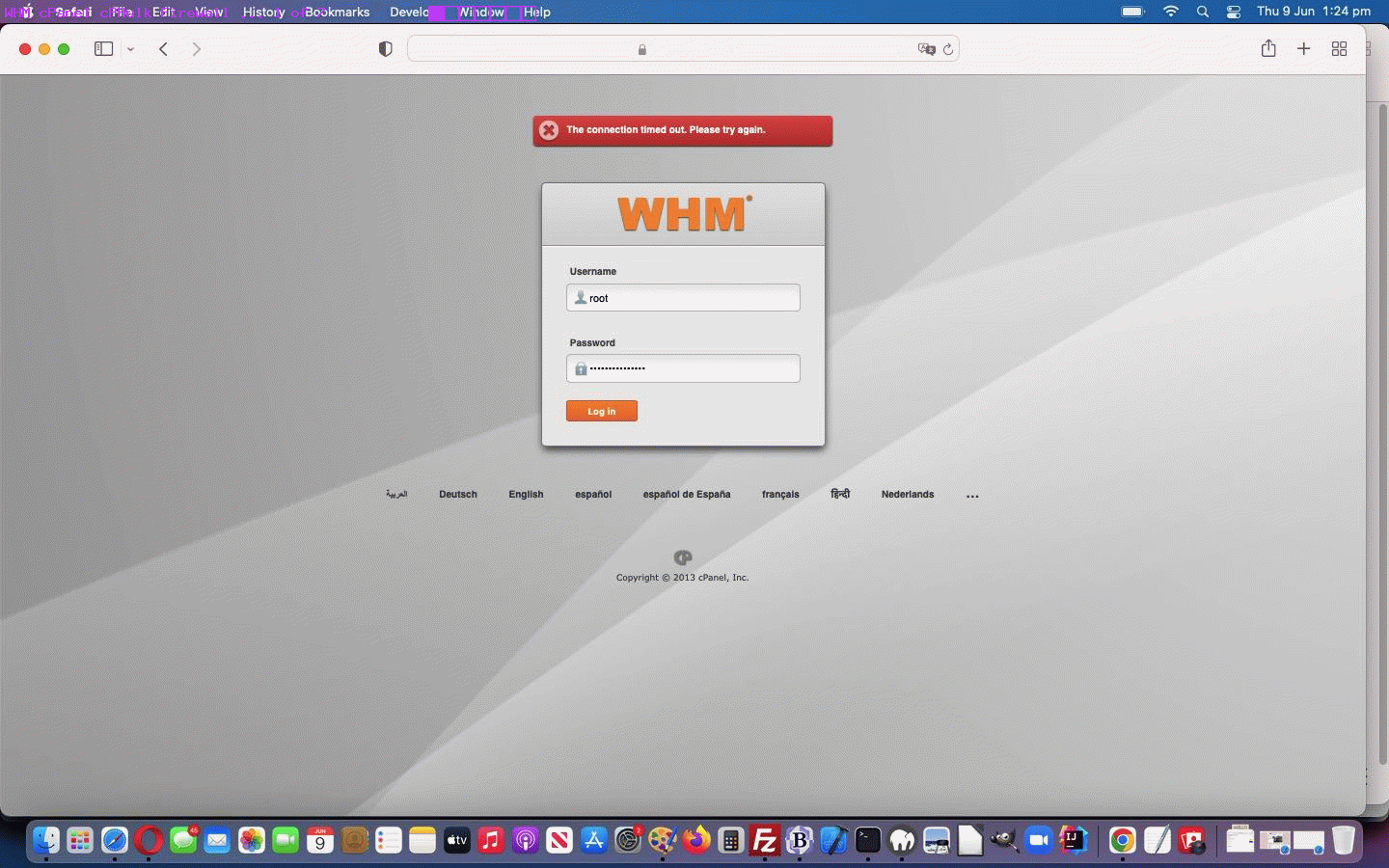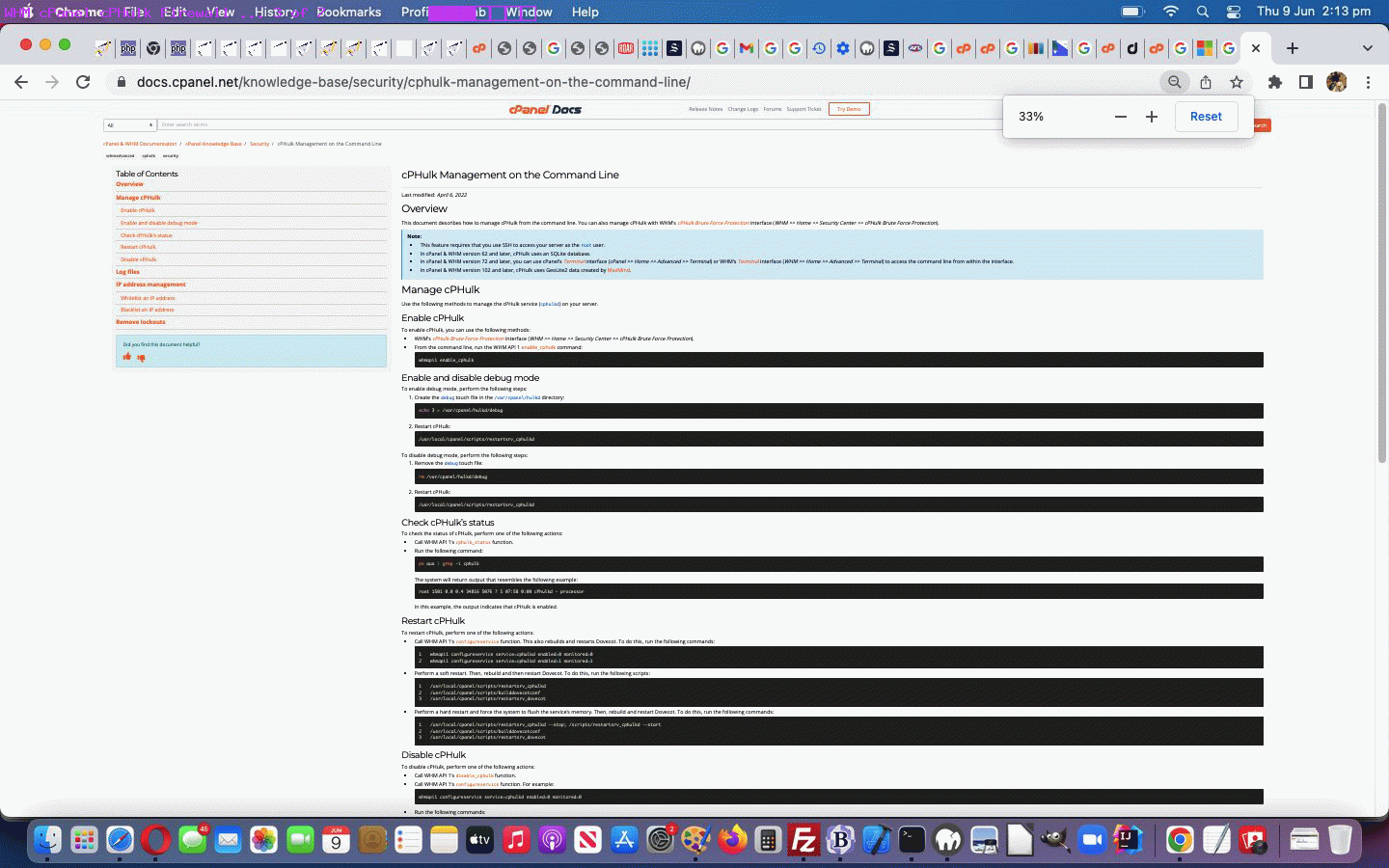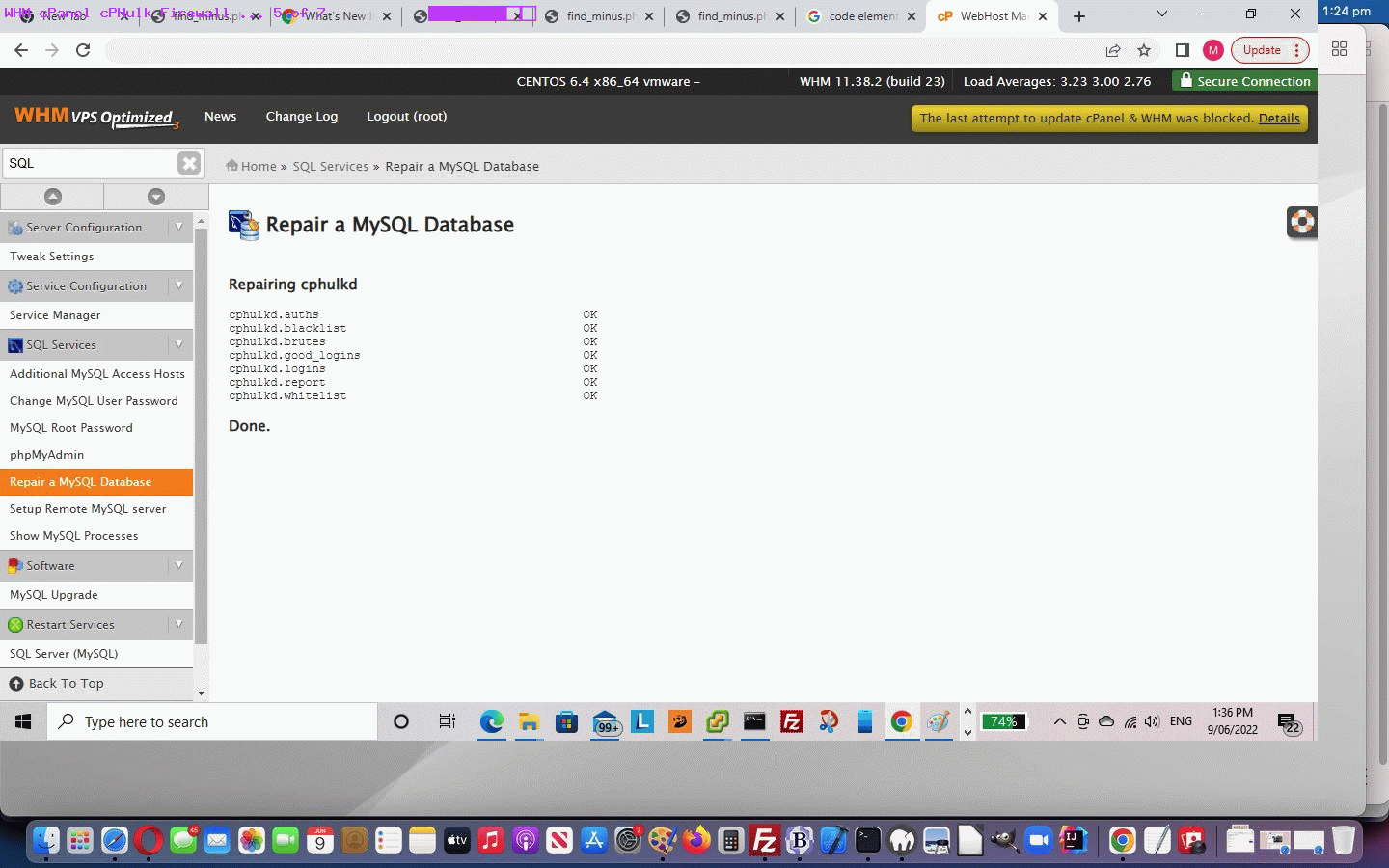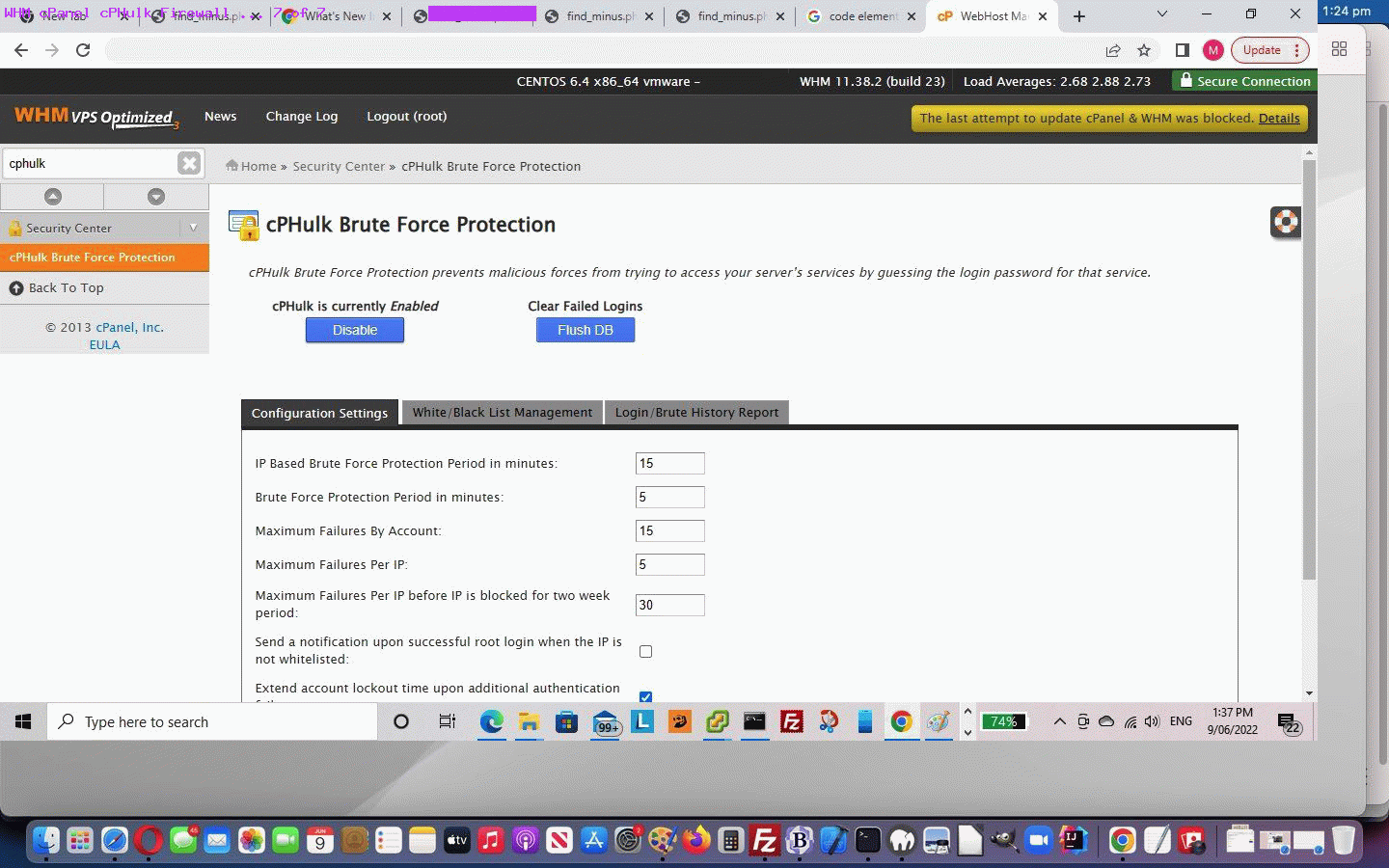
Researching this got us to try, thanks …
Main >> SQL Services >> Repair a MySQL Database
… successfully back at our graphical cPanel session. Then we clicked the “cPHulk is Currently Disabled … Enable” button to successfully get the Firewall functional again. Phew!
If this was interesting you may be interested in this too.
If this was interesting you may be interested in this too.