Some Apache/PHP/MySql web server cPanel configurations offer an option to directory protect a web server directory. We have a few questions …
- Why do this Apache web server directory protection?
- you may be developing and testing an incomplete website’s coding, as a programmer, and not want to allow access to the general public as this testing phase continues … on this, please see “Did you know?” section below as well
- it may be a way to put off hackers
- How does this work?
- for any one web browser session the first access to an Apache web server protected directory the user will be asked for the authorization username/password … and succeed with subsequent access to this and other non-protected areas of the website visited during that web browser session
- the Apache web server protected directory can be unprotected in cPanel as a separate operation later, as required
- When does this happen?
- as soon as the cPanel settings are saved …
- there is no need to restart the Apache httpd service to make this start happening
- Where do you go in cPanel to start the ball rolling?
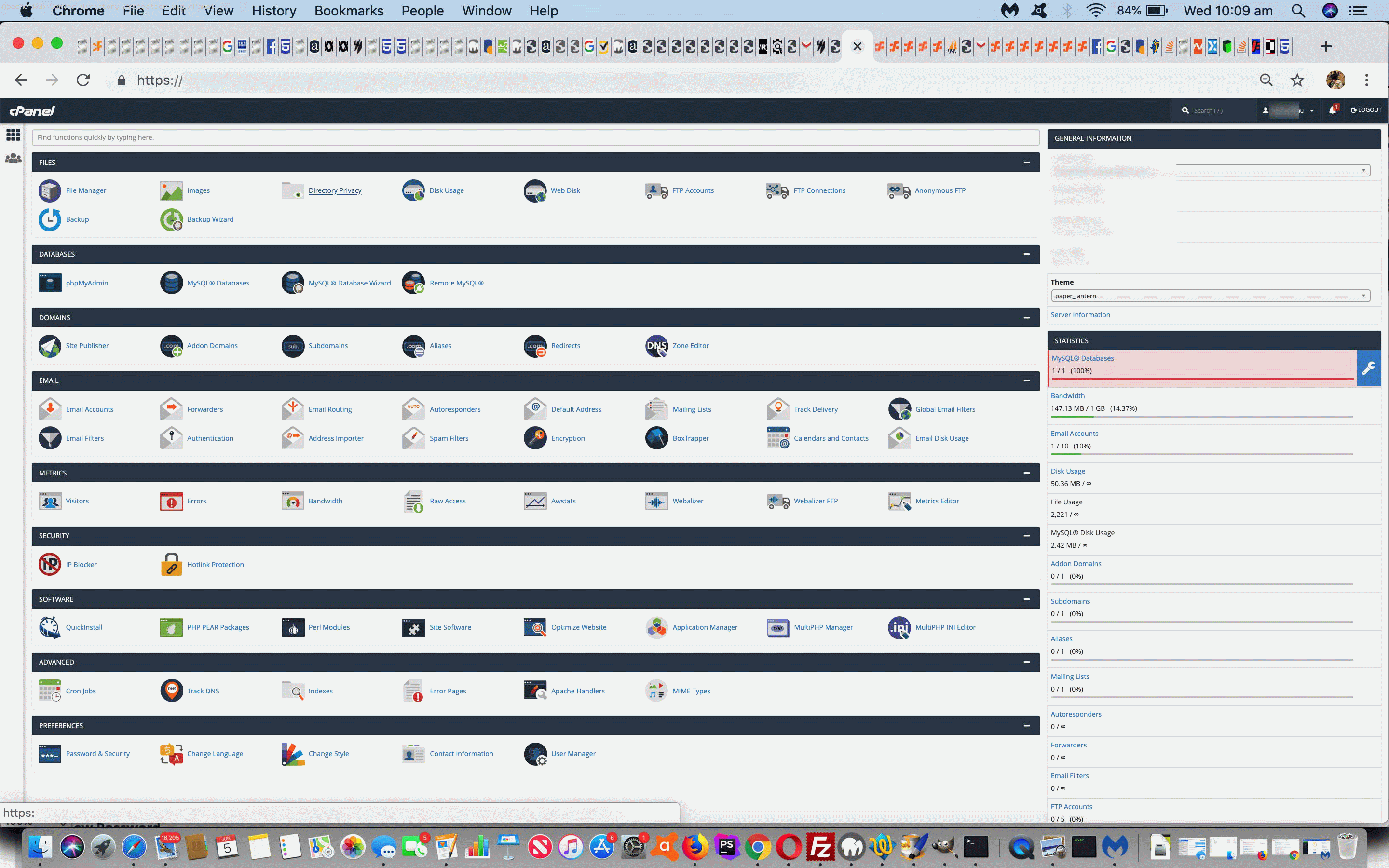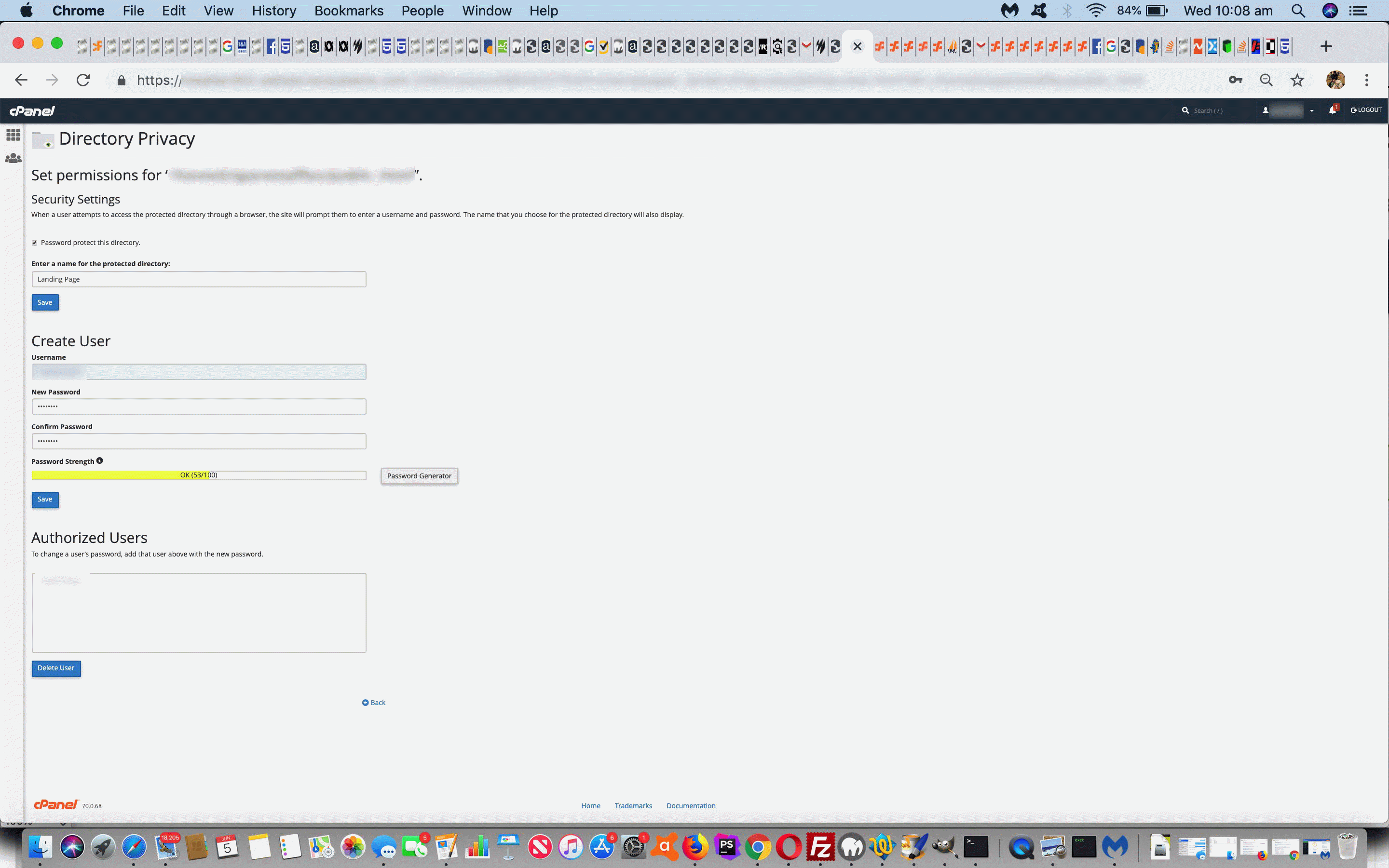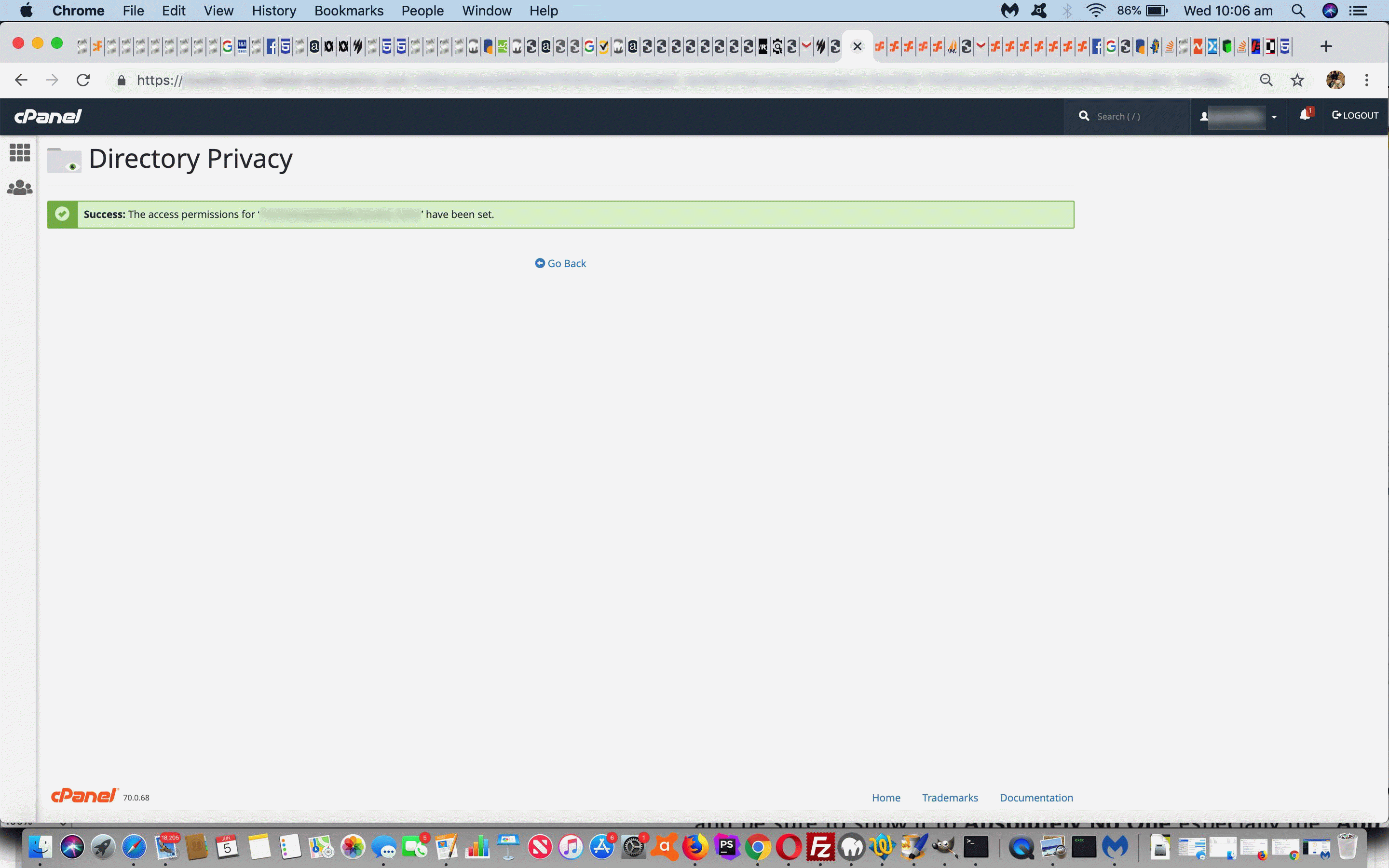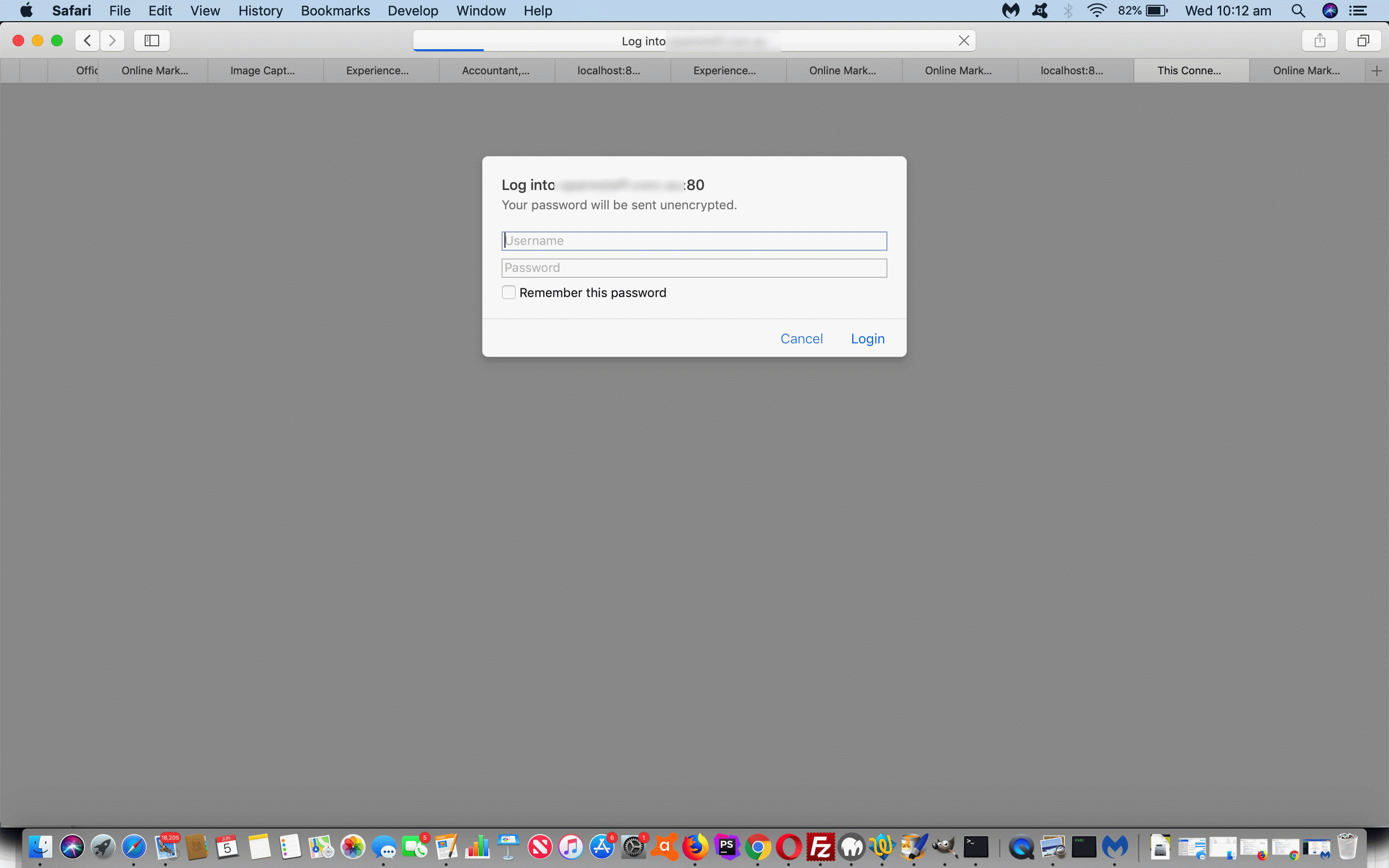
- each cPanel configuration can be different but if there is a “Files” set of icons a “Directory Privacy” icon would be apt …
- search for “Directory Privacy” in the “Search” textbox of cPanel … noting that some Apache web servers do not offer this functionality
We hope this clarifies a programmer’s view of this issue. We’re pretty sure there will be other reasons to use this feature by webmasters out there in the “net” wooooooorrrrrrlllllld.
Did you know?
As far as privacy goes there is (web server) “directory level” protection, as above, and then there is the attempt to not be discovered by Search Engines as another matter entirely. Supposing you are halfway through developing a website, are testing migration issues with the live public domain URL of the website, but do not want to be “discovered” (by search engines) in the meantime? No guarantees, but the search engines may look for a “robots.txt” file placed in the website root directory to honour any “Disallow” clauses such as …
User-agent: *
Disallow: /config
Disallow: /index.php
… respectively for (the case of) a web server directory and (the case of an) individual file.
If this was interesting you may be interested in this too.