A couple of days back on our Macbook Pro laptop I had occasion to think about our home cable and wireless network (equals “some of our” work cable and wireless network). Have you gone for a nap?! Most people have that reaction.
Why aren’t there “home wifi and wireless and whatever whisperers”? That’s all we want … whisperers. It shouldn’t be that it has to be reset and jiggered with all the time. But wireless does have its issues.
We have a cable network to the front of the house where there is a Netgear cable modem CG3100D, then some ethernet connects this to a Dlink DI-524 Wireless Router, as you can see …
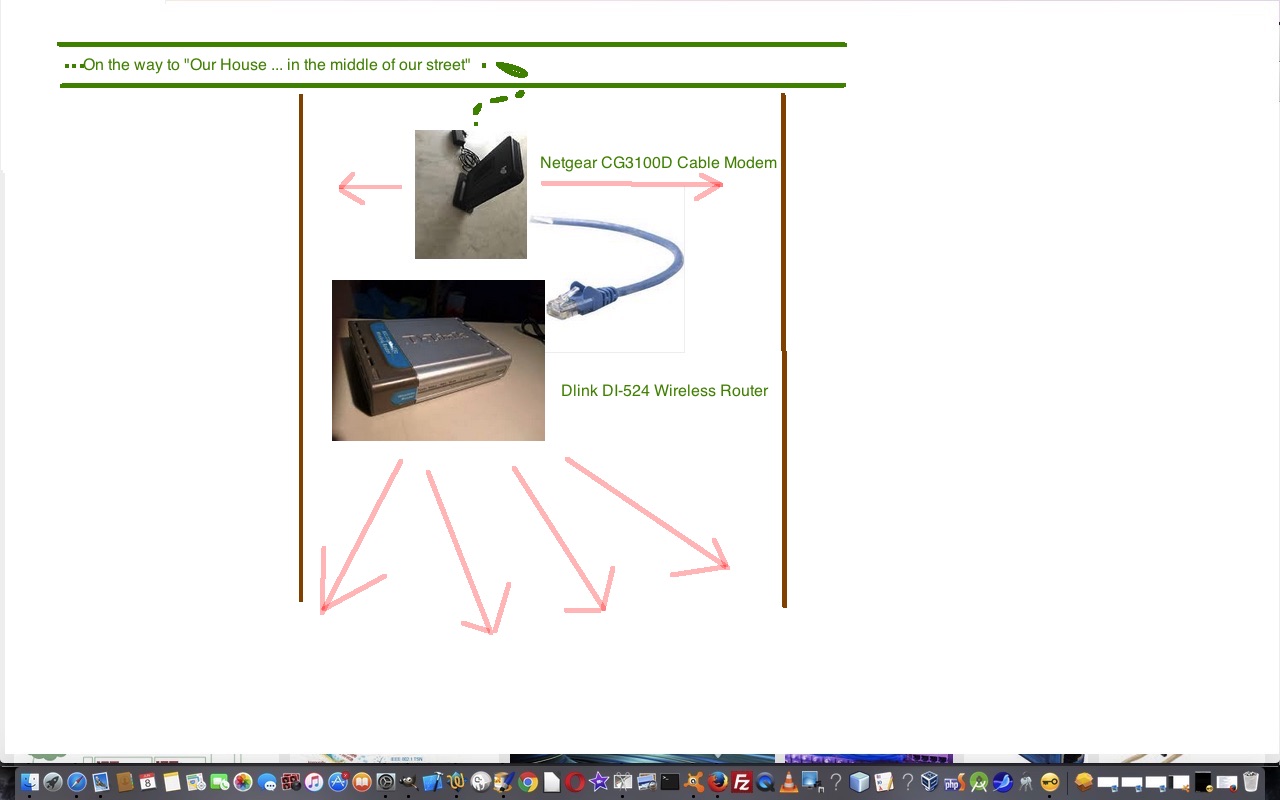
… here … and, for the first time, our wireless failed but the cable modem was okay. We can have all of it fail if the ISP arrangements to the cable modem fail, but this was not the case.
So thought about this and decided to effectively rename our wireless router, and in the meantime, give it a new WEP HEX password.
During that rejigging, I got to a “dumb point” where I tried deactivating DHCP on the wireless router … please, never do this yourself without good reason, and got to a point where the wireless router couldn’t be reached, and so did a reset (to factory settings) of the wireless router … again, this should not have to happen … anyway, as we were saying, got to a second tricky point where the cable modem was still working, but coming off the wireless router reset, and a session with http://192.168.0.1 as per “ethernet connected” Dlink instructions, rename and change of WEP HEX password twice … don’t ask … got the following message ….
Wi-Fi has the self-assigned IP address xxx.xxx.xxx.xxx and will not be able to connect to the Internet.
… when in Apple -> System Preferences -> Network -> WiFi (on and connected) and pointing at the Dlink wireless router … as the juxtaposition of what happened DHCP enabled as the Dlink wireless router default would want.
Didn’t like the look of that … though it was an improvement on the “dumb fish” looks you give yourself using any type of “Network Diagnostics” application methods I’ve ever seen and used … though that could be a “user related issue” … chortle, chortle … at least there was a good error message thought to send to Google … and that got me finally onto the basis for the topic of today’s tutorial … the context and importance of Keychain Access, as Mac OS X calls this important utility application.
Now I’ve been waiting some time to tell you about Mac OS X’s utility application Keychain Access, but you’ll have to bear with us in that, today, we only “dip our toes” into this vast and growing topic regarding modern day access and security on our networks.
So what is a “keychain”? Got surprised at Wikipedia with …
Keychain is password management system in OS X developed by Apple. It was introduced with Mac OS 8.6, and has been included in all subsequent versions of Mac OS, including OS X.
… that it is so Mac-centric, but, anyway, it is used regarding the storing of your (if you have one, and use a Mac) wireless router’s WEP HEX password. Us stuffing up, and redoing it in amongst all the rejigging meant that the password stored in that …
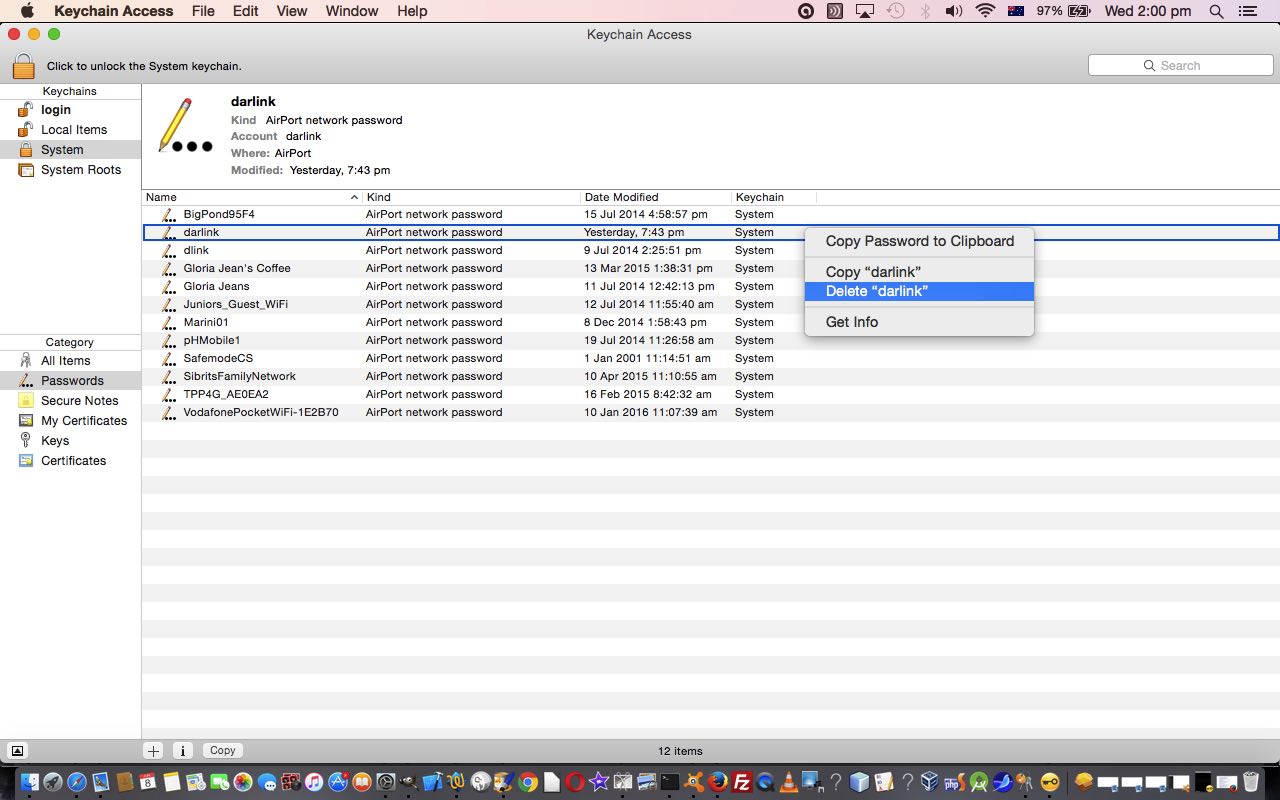
Keychain Access -> Keychains = System -> Category = Passwords -> Entry = "darlink" (ie. the new name for our Dlink wireless router)
… was wrong … and would stubbornly stay wrong without deleting its Keychain Record, forcing the next WiFi (on) reconnect to “darlink” attempt would reask for the WEP HEX password.
So there you go … that fixed it for that error up above.
And this represents our first dip into “Keychain Access”, which we notice, on a Mac, at the very least, involves itself in …
- login keys
- login passwords
- Airplay Client Identities
- Airplay Client Peers
- local passwords
- web (form) passwords
- certificates
-
Keychain Access is a Mac OS X application that allows the user to access the Keychain and configure its contents, including passwords for websites, web forms, FTP servers, SSH accounts, network shares, wireless networks, groupware applications, encrypted disk images, etc. It unlocks, locks, and displays passwords saved by the system which are dynamically linked to the user’s login password, as well as managing root certificates, keys, and secure notes.
We hope to come back to this topic at a later date.
If this was interesting you may be interested in this too.