Yesterday’s Exim Mail Server Troubleshooting Primer Tutorial represented a mail server level of issue with emailing hereabouts.
Another level of issue with emailing can occur with our inhouse PHP created inline HTML emails to Gmail, where we’ve again used Exim‘s exim_mainlog log file to discover …
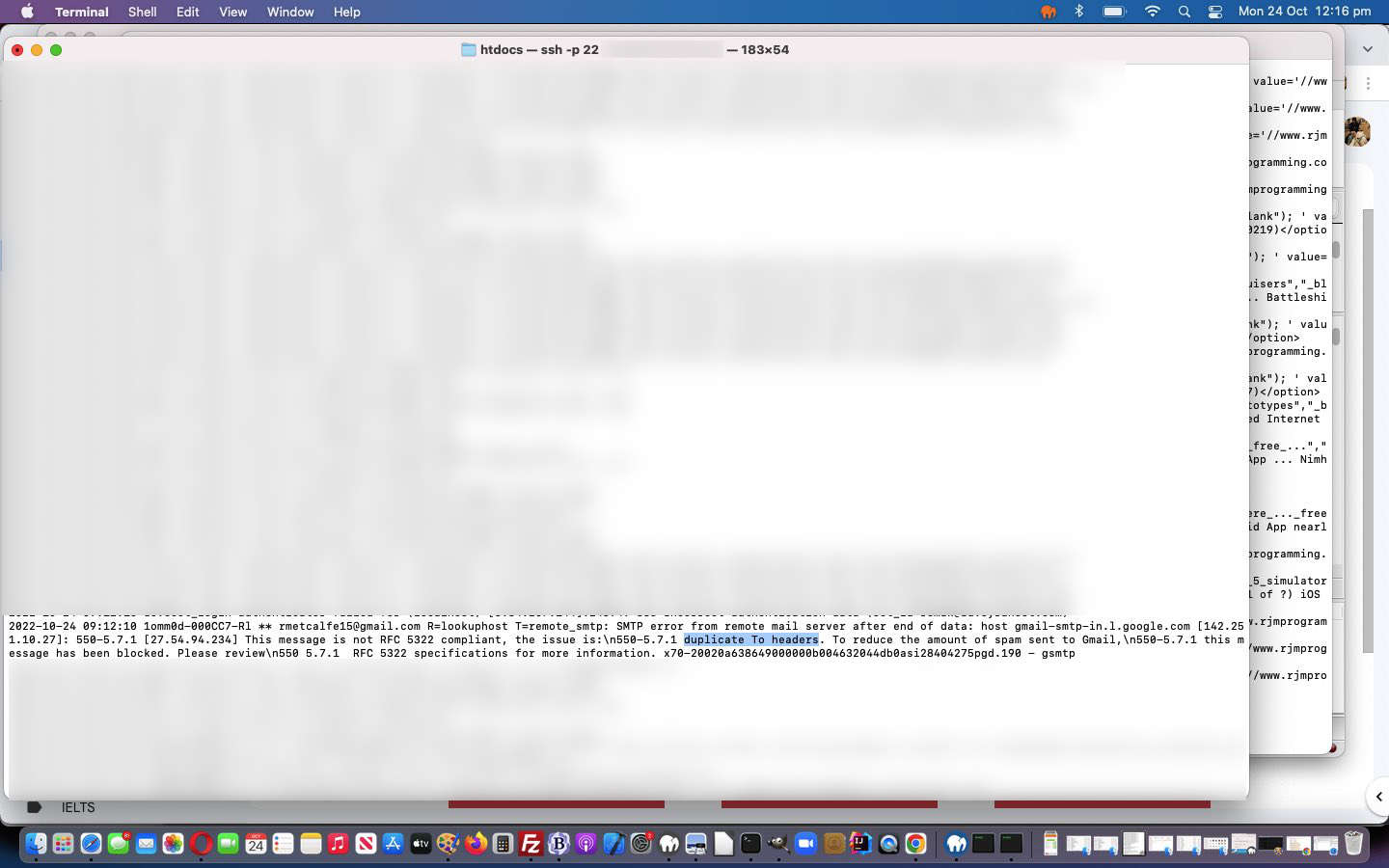
… whereby we’d been, in the headers of the PHP mail email message, specifying the “To:” field twice, and at the Gmail end, this email is blocked until we modified PHP as per …
<?php
if ($message != "") { // inline HTML
// To send HTML mail, the Content-type header must be set
$hdrs[] = 'MIME-Version: 1.0';
if ($subd != "") {
$hdrs[] = 'Content-type: application/pdf';
} else {
$hdrs[] = 'Content-type: text/html; charset=iso-8859-1';
}
// Additional headers
if (strpos(strtolower($to), "@gmail.com") === false) { //!in_array('To: ' . $to, $hdrs)) {
$hdrs[] = 'To: ' . $to;
}
$hdrs[] = 'From: ' . $fromer;
if ($cc != "") { $hdrs[] = 'CC: ' . $cc; }
if ($bcc != "") { $hdrs[] = 'BCC: ' . $bcc; }
$hdrs[] = 'Reply-To: ' . $fromer;
// Mail it
$fflist="inline HTML";
zmail($to, $subject, $message, implode("\r\n", $hdrs));
} else {
zmail($to, $subject, "", $headers);
}
?>
… in the changed inhouse PHP email helper emailhtml.php to remedy this situation.
Did you know?
Though the exim_mainlog panned out to be telling the truth, we wanted to see the issue for ourselves. Fortuitously, yesterday’s allowed through inline HTML email example was also an example of leniency at Gmail (as well as engendering a false sense of security) to allow through and we were able to reference that email’s vertical “ …” menu’s “Show original” suboption to see the duplicate ‘To:’ header fields that would later cause another blockage. The “Show original” suboption here can be very useful.
And on macOS or Linux command line, in dynamic logging situations, the (in our case) …
# tail -f /var/log/exim_mainlog
… followed by the sending of an inhouse PHP mail created inline HTML email, and then after a bit, control-C back at the tail operation, was a good way to investigate a little subset of relevant logging activity, via the macOS Terminal application scrolling (up) abilities.
Previous relevant Exim Mail Server Troubleshooting Primer Tutorial is shown below.
Exim Internet Mailer, as our Mail Server software here at this RJM Programming web server, has seemed an enigma, especially when, a while back (tut, tut) it went quite quiet sending out emails to Gmail recipients, at the very least. Take a look at the directory structure of exim, and you might join me!
However, today, we stepped back and got past our vague “spam” theories, and got inspiration from the excellent advice at send a testmail via exim – makandra Operations, thanks, to try, at our RJM Programming ssh access terminal command line session, typing …
# exim -v rmetcalfe15@gmail.com
From: user@domain.name
Subject: Foobar
Text Text Text
I like Pie!
<control-D>
… ended by (macOS keyboard) control-D to get to see the exim error logging dynamically. Was it the monochrome colour and scrolling movement that finally got me to take my head out of the sand?!
The logging that followed reasoned …
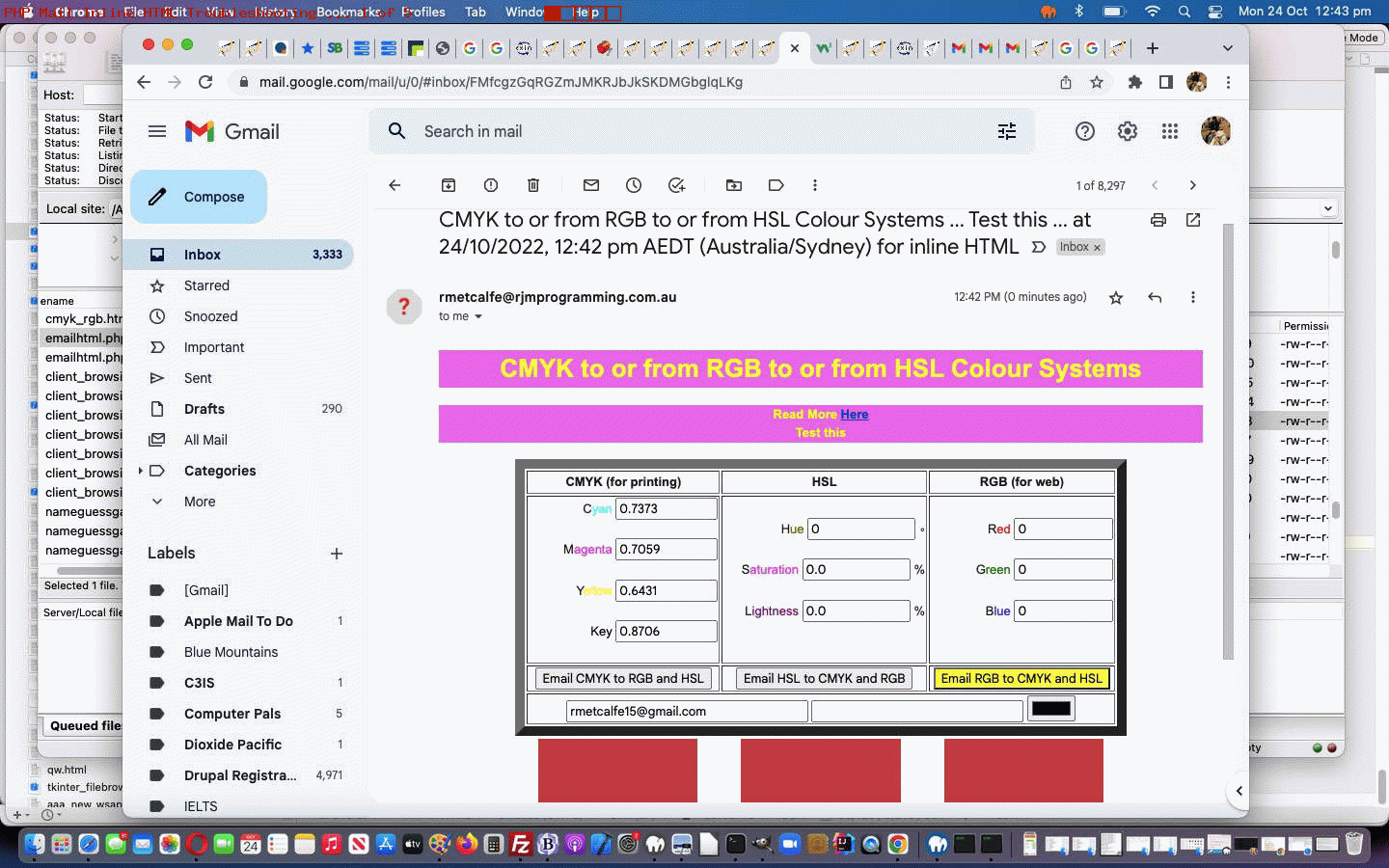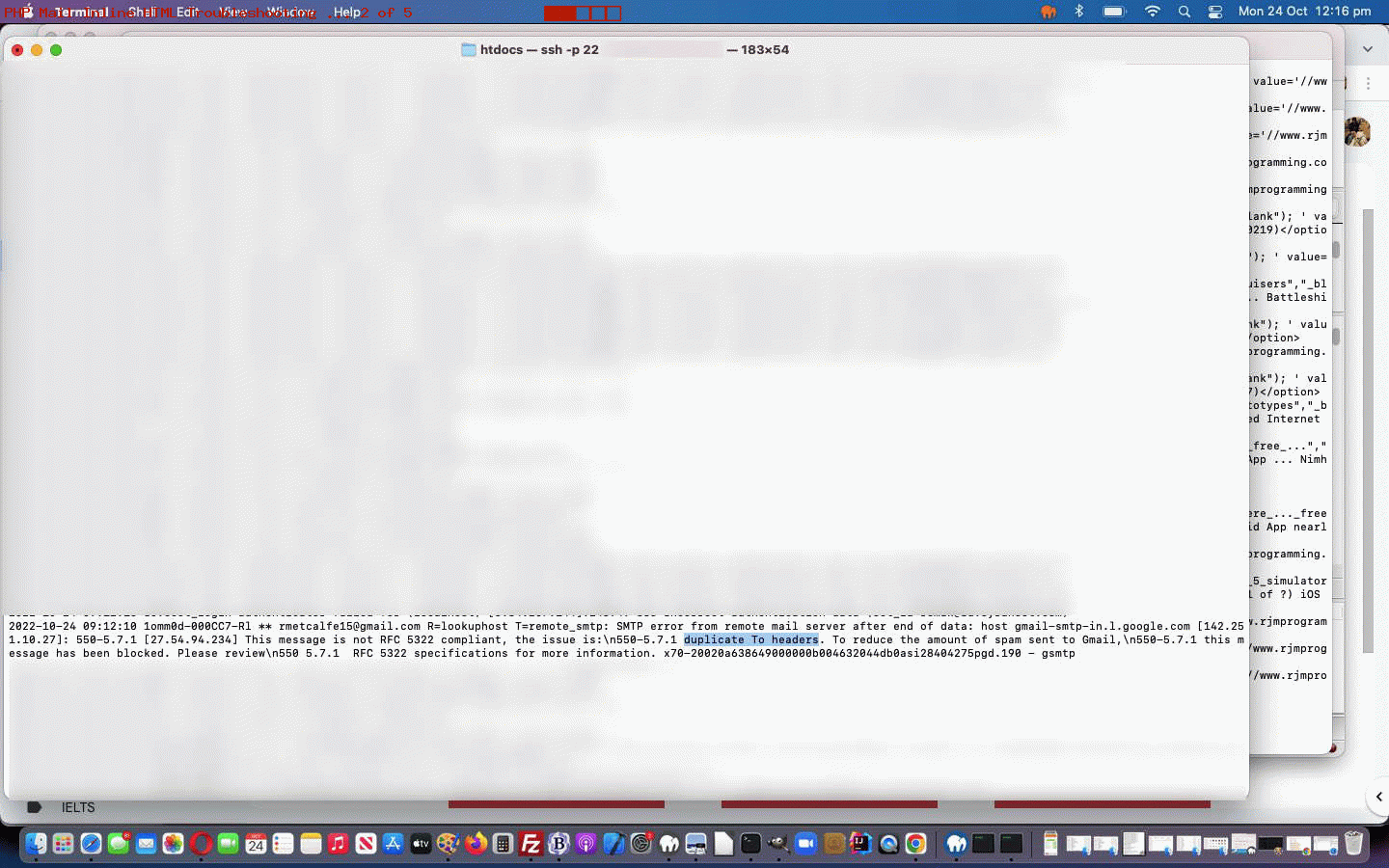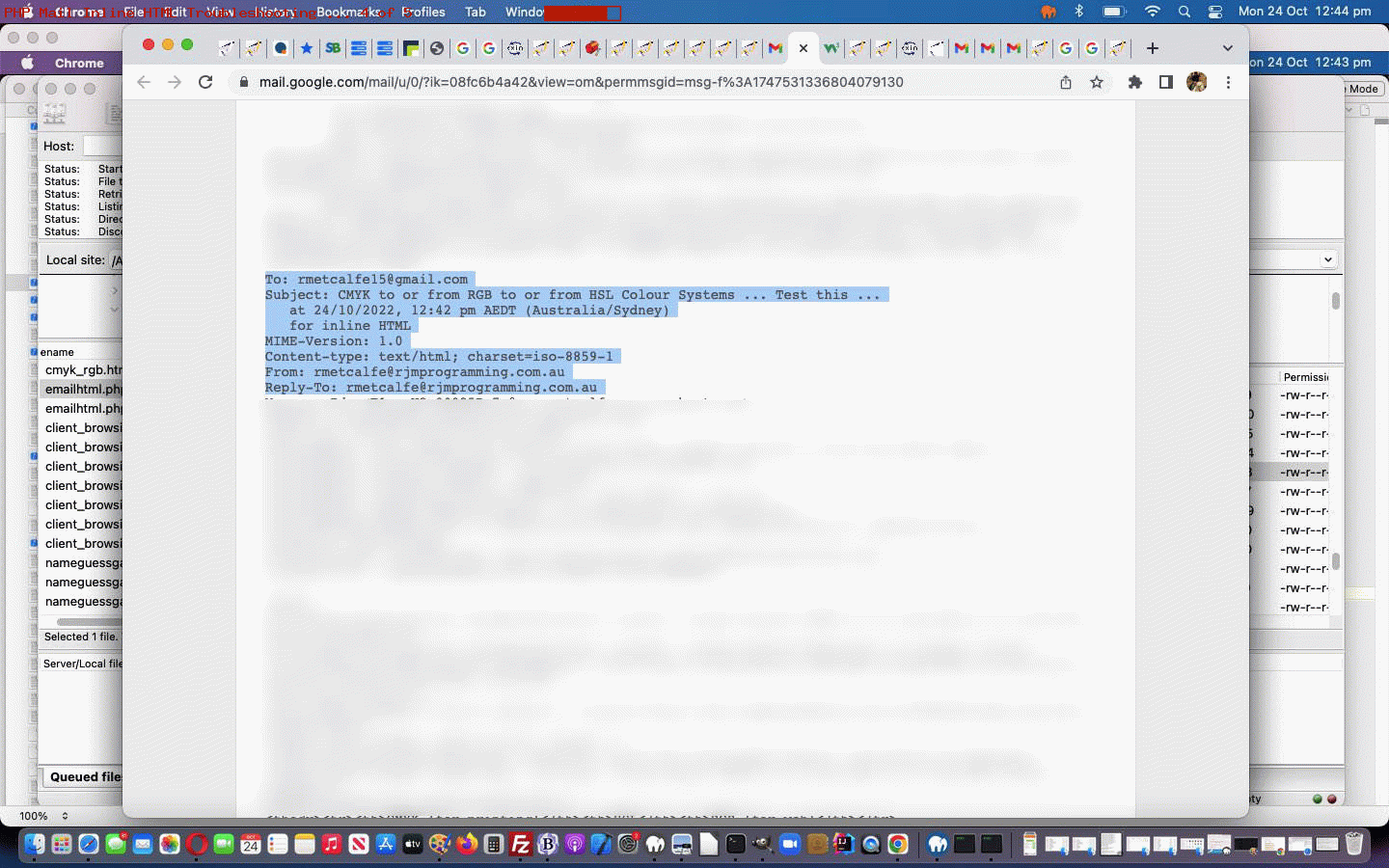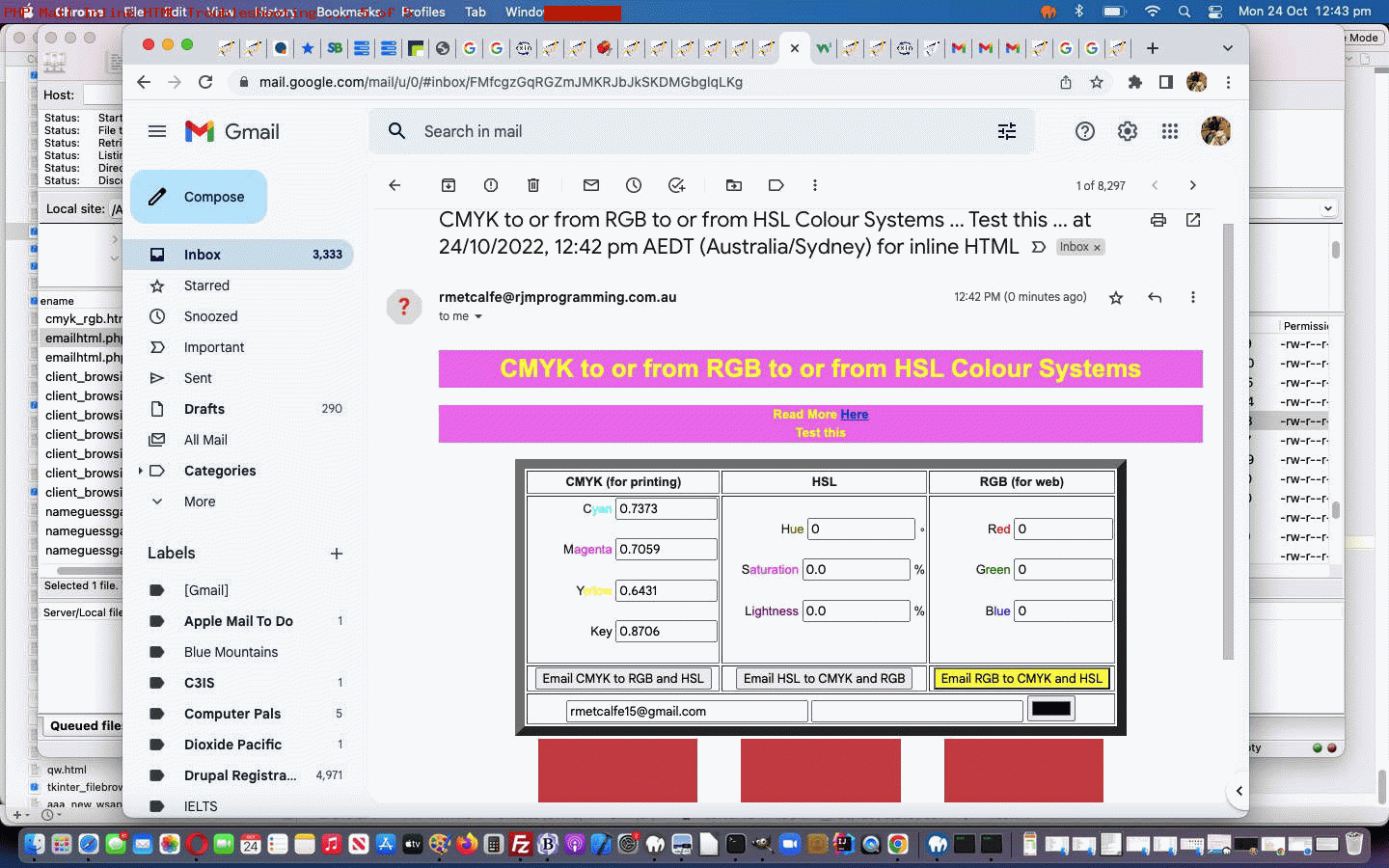
SMTP error from remote mail server after end of data: host gmail-smtp-in.l.google.com: 421-4.7.0 This message does not pass authentication checks (SPF and DKIM both do\n421-4.7.0 not pass). SPF check does not pass\n421-4.7.0 with ip.To best protect our users from spam, the\n421-4.7.0 message has been blocked. Please visit\n421-4.7.0 https://support.google.com/mail/answer/81126#authentication for more\n421 4.7.0 information.
… and gave me a link to follow up with at Prevent mail to Gmail users from being blocked or sent to spam – Gmail Help, thanks, which honed my attention to possible need for, first off …
- SPF record
- DKIM record
… ahead of realizing, sadly, that no cPanel menu options directly attended to this on the RJM Programming’s cPanel, but a great link Add SPF Records and DKIM keys in cPanel Using CLI HostnExtra, thanks, coming to my aid, filling me with enough confidence, that its suggested …
# /usr/local/cpanel/bin/dkim_keys_install [user]
# /usr/local/cpanel/bin/spf_installer [user]
… “single user” may indeed suit RJM Programming for three reasons …
- going …
# ls -l /var/cpanel/users
… implied just the one [user] needed, to worry about - /usr/local/cpanel/bin/dkim_keys_install script exists
- /usr/local/cpanel/bin/spf_installer script exists
So we plucked up the courage to proceed with those excellent suggested commands just above (substituting [user] for our RJM Programming web site’s user name), with great success!
# exim -v rmetcalfe15@gmail.com
LOG: MAIN
cwd=/var/cpanel/users 3 args: exim -v rmetcalfe15@gmail.com
From: user@domain.name
Subject: Foobar
Text Text Text
I like Pie!
LOG: MAIN
<= user@domain.name U=root P=local S=392 T="Foobar"
[/var/cpanel/users]# LOG: MAIN
cwd=/var/spool/exim 4 args: /usr/sbin/exim -v -Mc 1omQjv-000CHd-L7
delivering 1omQjv-000CHd-L7
Connecting to gmail-smtp-in.l.google.com [an.ip.address]:25 ... connected
SMTP<< 220 mx.google.com ESMTP [google-code].65 - gsmtp
SMTP>> EHLO vs-rmetcalfe.au.syrahost.com
SMTP<< 250-mx.google.com at your service, [ip.rjm]
250-SIZE 157286400
250-8BITMIME
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-CHUNKING
250 SMTPUTF8
SMTP>> STARTTLS
SMTP<< 220 2.0.0 Ready to start TLS
SMTP>> EHLO domain.name
SMTP<< 250-mx.google.com at your service, [ip.rjm]
250-SIZE 157286400
250-8BITMIME
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-CHUNKING
250 SMTPUTF8
SMTP>> MAIL FROM:<user@domain.name> SIZE=1426
SMTP>> RCPT TO:<rmetcalfe15@gmail.com>
SMTP>> DATA
SMTP<< 250 2.1.0 OK [google-code].65 - gsmtp
SMTP<< 250 2.1.5 OK [google-code].65 - gsmtp
SMTP<< 354 Go ahead [google-code].65 - gsmtp
SMTP>> writing message and terminating "."
SMTP<< 250 2.0.0 OK 1666492215 [google-code].65 - gsmtp
SMTP>> QUIT
LOG: MAIN
=> rmetcalfe15@gmail.com R=lookuphost T=remote_smtp H=gmail-smtp-in.l.google.com [an.ip.address] X=UNKNOWN:ECDHE-ECDSA-AES128-GCM-SHA256:128
LOG: MAIN
Completed
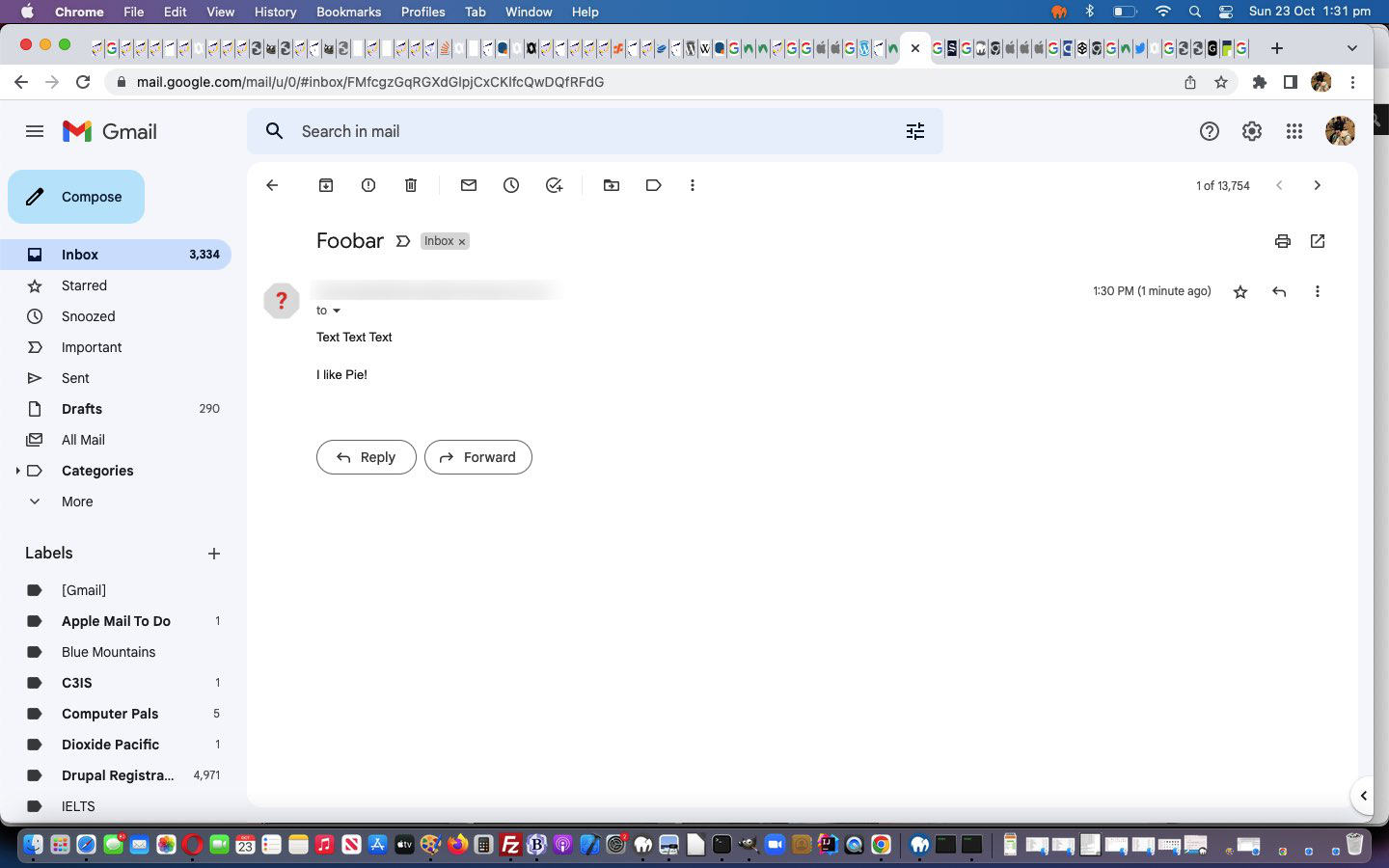
Yayyyyyy!
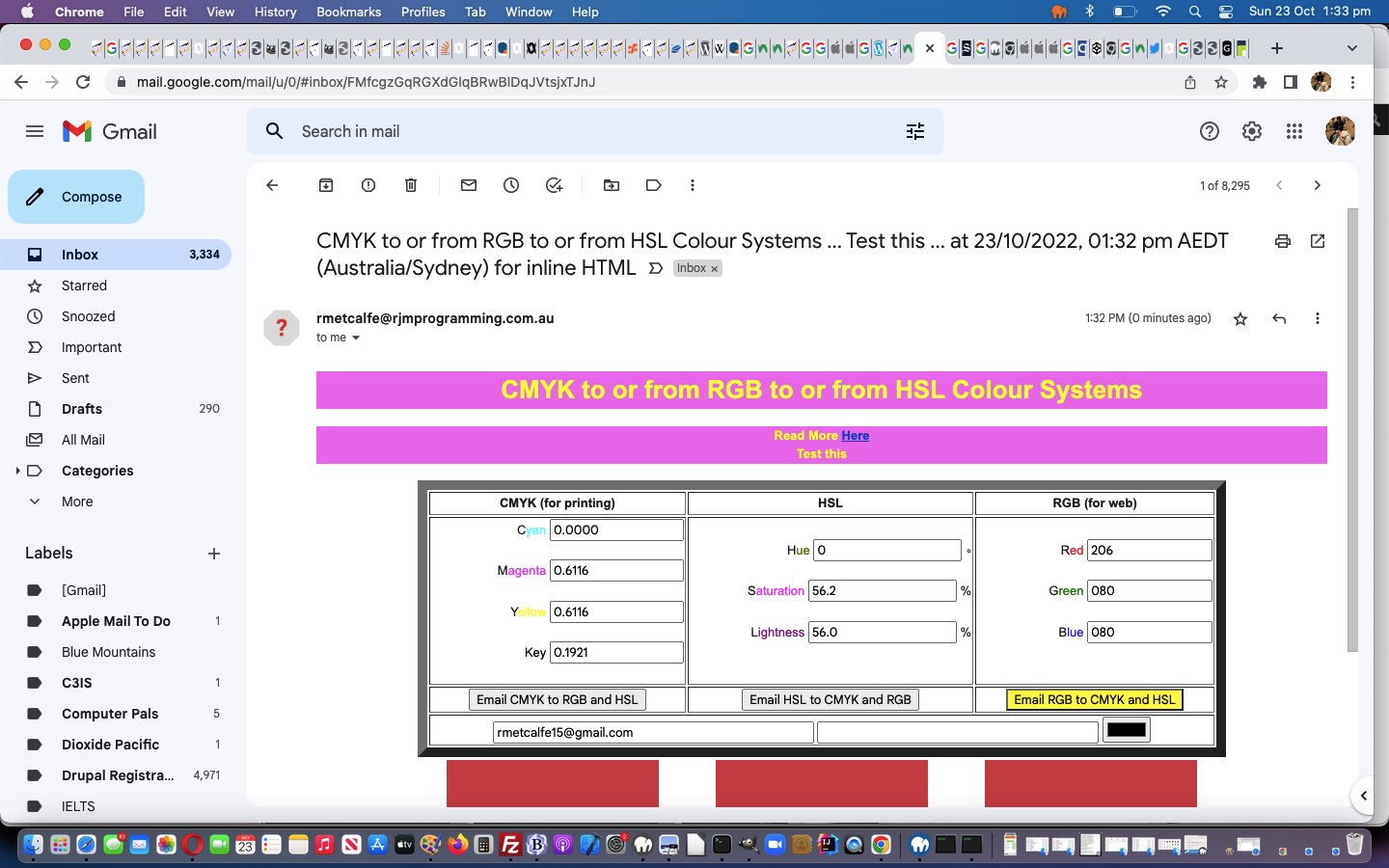
And yayyyyyy to an inline HTML email scenario too!
If this was interesting you may be interested in this too.
If this was interesting you may be interested in this too.