Two Factor Authentication has been the response of many software developers towards measures to shore up security on their products, regarding “Identity Theft”. This method of confirming a real human’s identity …
Multi-factor authentication (MFA) is an authentication method in which a computer user is granted access only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something the user and only the user knows), possession (something the user and only the user has), and inherence (something the user and only the user is).[1]
Two-factor authentication (also known as 2FA) is a type, or subset, of multi-factor authentication. It is a method of confirming users’ claimed identities by using a combination of two different factors: 1) something they know, 2) something they have, or 3) something they are.
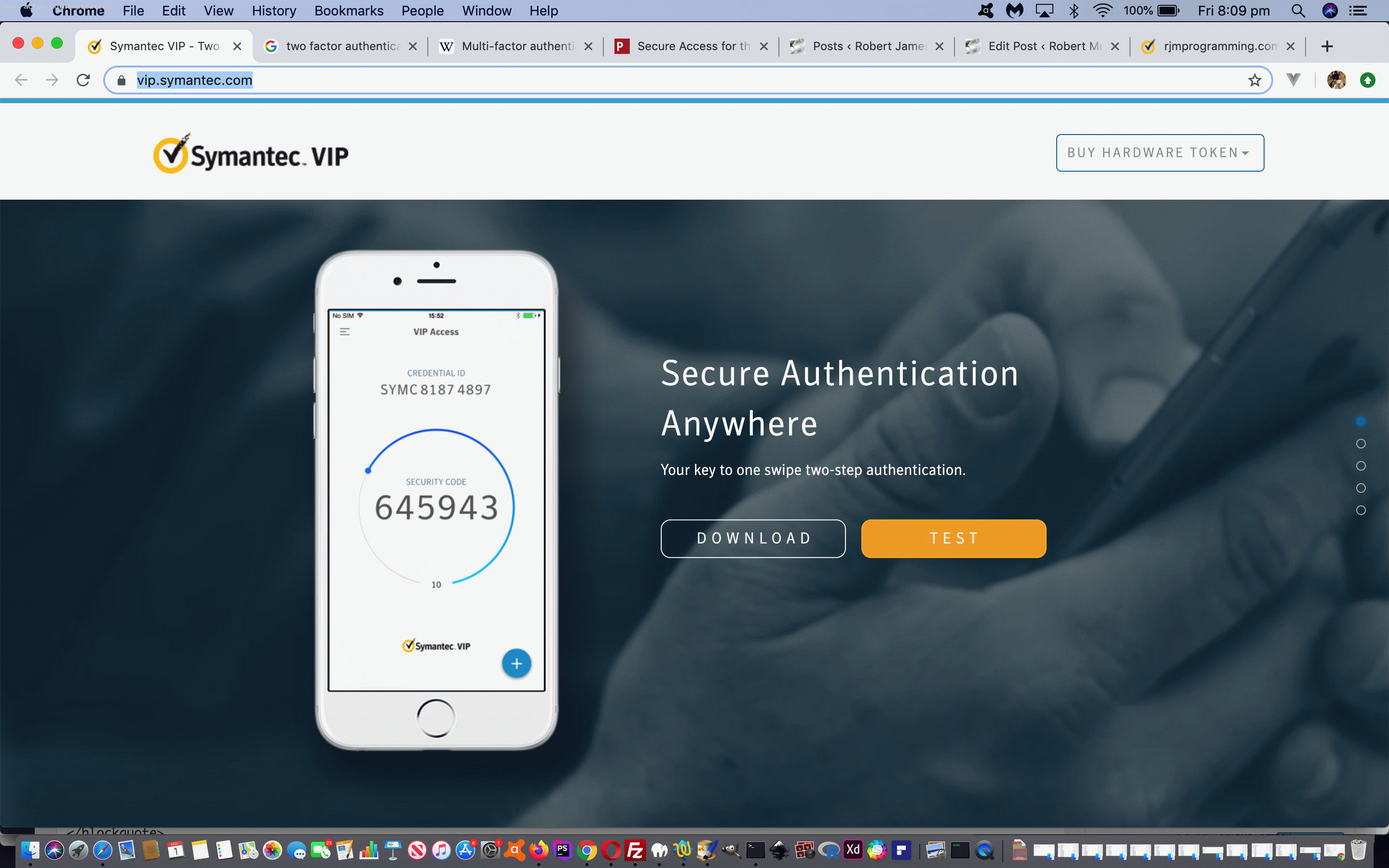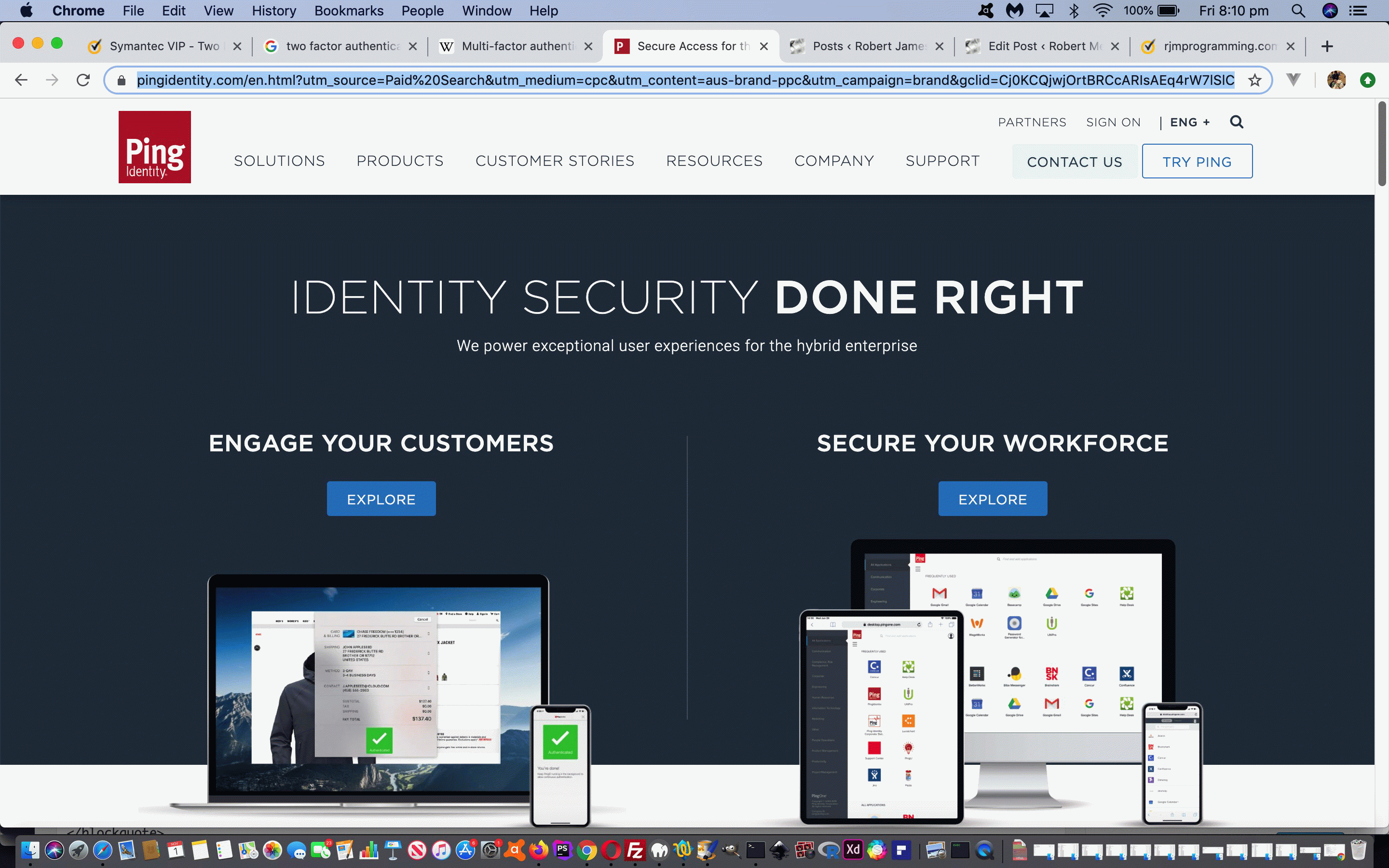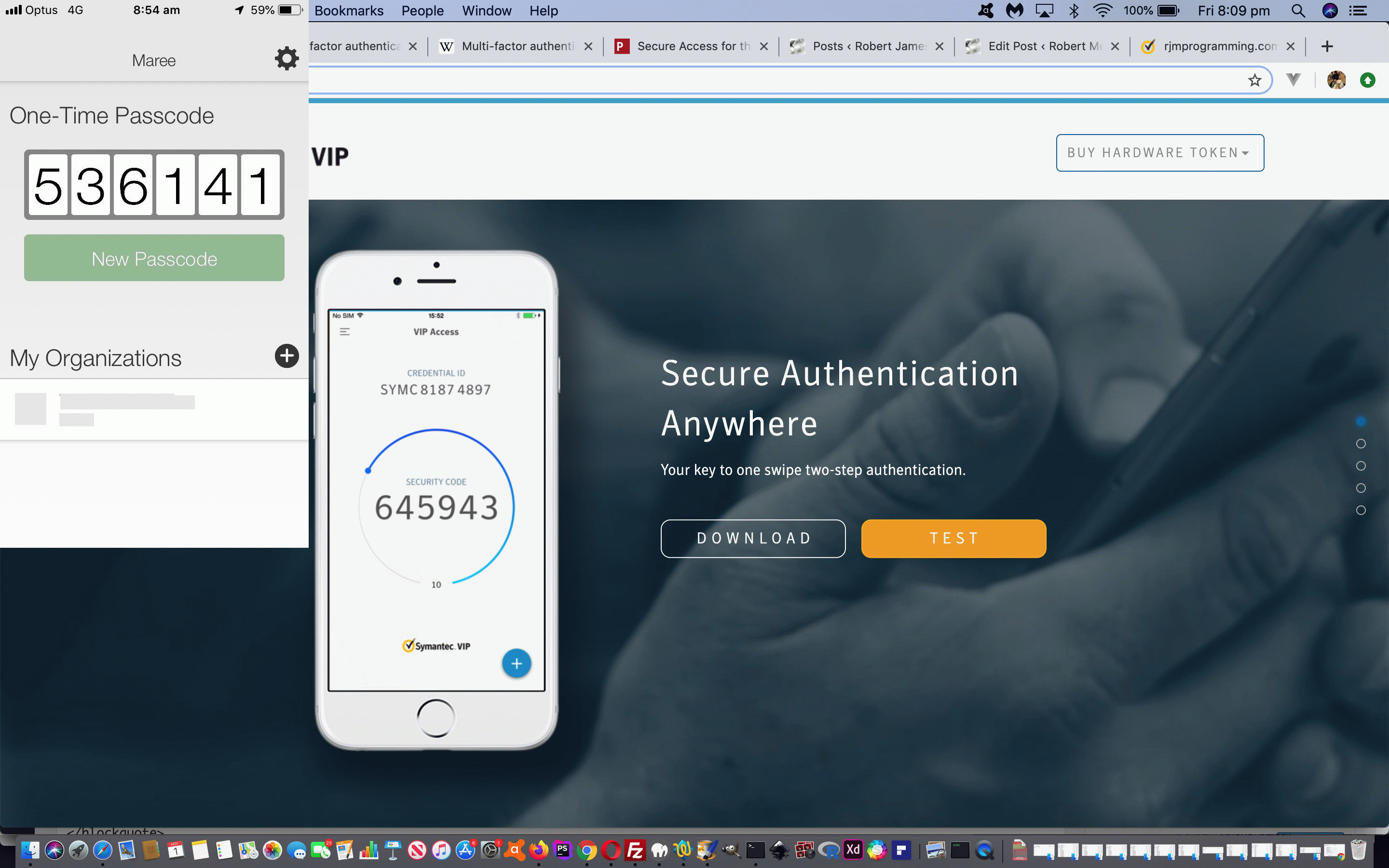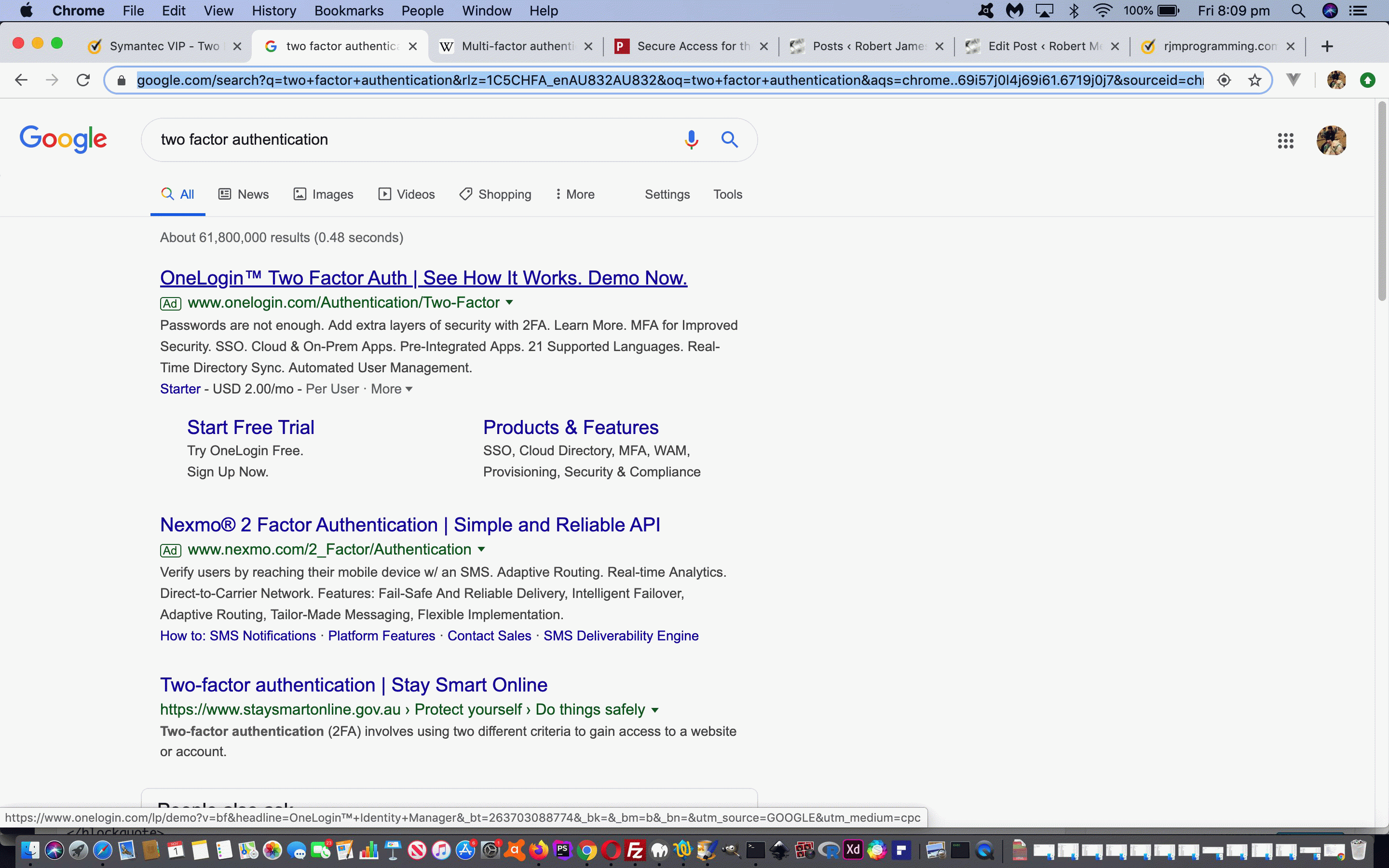
… is, of course, a major step forward for software to know it is reaching the real audience it was intended for. We have seen it most with “2) Something they have” above, in practice. A software component will get you to login to their software, as well as get you to verify a third identifier (on top of username and password) on an associated (usually) mobile device you create the association with on signing up with that software.
Two mobile device apps we’ve used in this two factor authentication line of work are …
- VIP Access by Symantec
- Ping Identity
… both of which offer the security service of providing a randomised large integer third proof of identity to match up with the software product sign in at a given snapshot of time. Secure and simple, but asking for lots of proof! In this day and age, though, with more and more mission critical software entering the scene, a growing requirement. We’ll leave you with What is Two-Factor Authentication (2FA) and How Does It Work?‘s excellent image to explain Two Factor Authentication, below …

If this was interesting you may be interested in this too.